
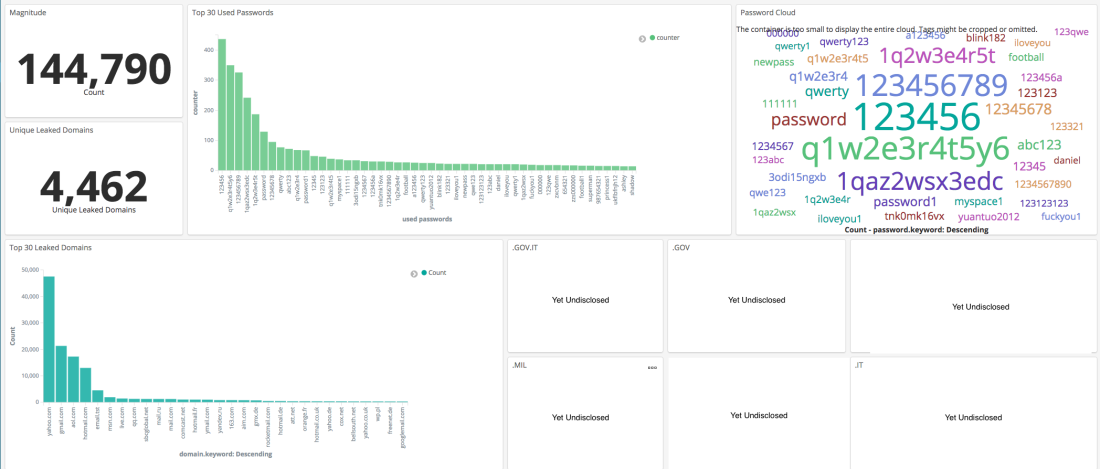
One of the first questions I wanted to answer was: “What are the most used passwords ?“. I am aware that many researches wrote about the most used passwords, but now I do have the opportunity to measure it. To get real used passwords and to evaluate the reality. So let’s see what are the most used passwords out there!
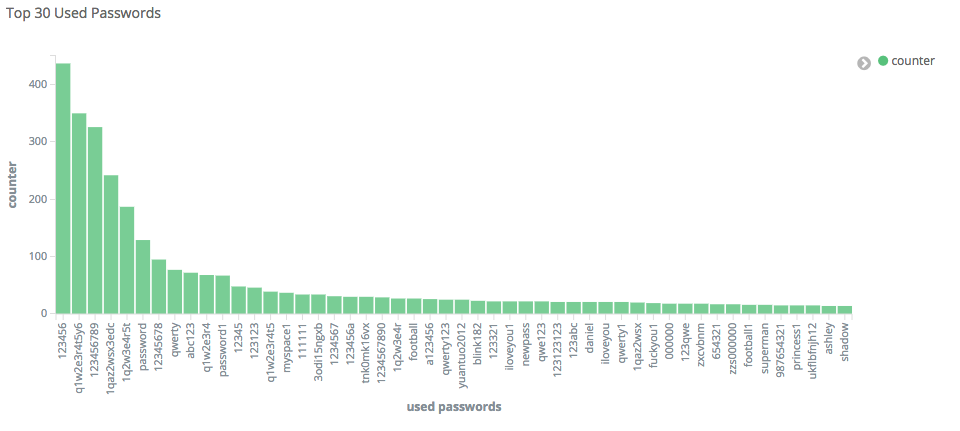
So far the most used passwords are: “123456”, “q1w2e3r4t5y6”, “123456789”, “1qaz2wsx3edc”, followed by most common passwords like “12345678” and “qwerty”. By observing the current graph and comparing it to common researches on frequently used passwords such as here, here, and here we might appreciate a significative difference: the pattern complexity! In fact, while years ago the most used passwords were about names, dates or simple patters such as “qwerty”, today we observe a significative increase in pattern complexity, but still too easy to be brute-forced.
A second question came by looking at leaked emails. “What are the domain names of the most leaked emails ?” Those domains are not the most vulnerable domains but rather the most used ones. So I’m not saying that those domains are/or have been vulnerable or Pwned, but I am trying to find what are the most leaked email providers. In other words if you receive an email from “@gmail.com” what is the probability that it has been leaked and potentially compromised ? Again I cannot answer to such a question since I do not have the total amount of “@gmail.com” accounts all around the word, but I think it might be a nice indicator to find out what are the most leaked email domain names.

The most leaked emails come from “yahoo.com”, “gmail.com”, “aol.com” and “hotmail.com”. This is quite interesting since we are mostly facing personal emails providers (domains) rather then professional emails providers (such as company.com). So apparently, attackers are mostly focused in targeting people rather then companies (maybe attacking not professional websites and/or distributing malware to people rather then companies domain names). Another interesting data to know is about the unique leaked email domain names: 4426, so far !
Finally, it would be great to know from what sources data is coming from ! At such a point I have no evidences of what I am going to write about, but I made some deductions from the data leaked structure. The following image shows collection-1 structure.

Each folder
Are you interested in Marco Ramilli’ conclusions? Give a look at his post:
https://marcoramilli.com/2019/01/19/collection-i-data-breach-analysis-part-1/
| [adrotate banner=”9″] | [adrotate banner=”12″] |
(
[adrotate banner=”5″]
[adrotate banner=”13″]

