
An overview of the science of the occult, that brings forth a new level of security in the age of digital privacy. Cryptology is the mathematical foundation of penetration testing and can be adopted as a resource for securing assets and communications. Join us in this quest into the science of occult.
Cryptology is the branch of mathematics that encompasses cryptography, cryptanalysis, Steganography and Lock picking. The etymology of the word is “kryptós +logos”, which means the study of the occult. Cryptography is a process in which an insecure message suffers a mathematical process generating a secure message from its process. The insecure message is called plaintext, and the encoded message is called ciphertext.
The reverse process of cryptography to obtain the plaintext from ciphertext is called cryptanalysis. Steganography is a mathematical function where a secret message is hidden in other secret messages. Lock picking is an attack in physical device of codification, where a key opens a lock.
Cryptology can give businesses and organizations a new degree of security when implemented by laying out an in-depth defense of data. A cryptograph algorithm, also called a cypher, is a mathematical function that is used for encryption and decryption of a message. Restricted algorithms maintain a secret how the algorithm works and can be compromised if the key is revealed to anyone. The range of all possible values of the key is called keyspace.
There are two types of symmetric algorithms: Symmetric and Public Key. Symmetric algorithms have the property of calculating the encryption key from the decryption key and vice versa. Symmetric algorithms can be divided into Block Ciphers and Stream Ciphers.
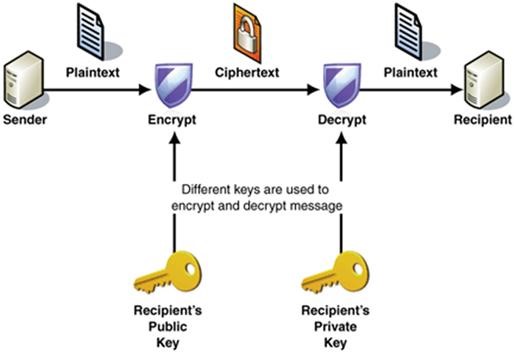
Public key algorithms, also called asymmetric algorithms, have the property of having a different encryption key for encryption and decryption. The decryption key cannot be calculated from the encryption key and the encryption key can be made public. The encryption key is called public key and the decryption key is called private key.
The main goal of cryptography is to provide confidentiality, authentication, integrity and nonrepudiation to the sender and the receiver of a communication. Cryptology is the mathematical foundation of modern day penetration testing. Penetration Testing uses some tools of cryptanalysis like THC Hydra in an attack, which is defined as a cryptanalysis attempt. The loss of a key through other means is called a compromise. Brute force, also called dictionary attack, is one case of cryptanalysis.
Cryptology is also related with penetration testing also in the security of the algorithm. Lars Knudsen classifies four types of breaking an algorithm: Total Break, Global Deduction, Instance Deduction and Information Deduction.
Cryptanalysis is used in Side Channel Attacks, where physical elements are analyzed and can give authorities and law enforcement agencies means of monitoring a suspect by generating a thermal image through the walls.
The Implications of the development of Cryptology and side channel attacks can permit law enforcement agencies a new degree of chain of custody with risking the lives of personnel while investigating suspects.
In Global Deduction Attack, cryptanalysis can find the key without knowing it but instead having an equivalent function that is accepted as the key. The study of discrete logarithms takes place in elliptic curves cryptanalysis, in which Pollard Rho attack is used to break into public key algorithms.
It is important to organizations and governments to develop and use Cryptology as a resource of protection aligned with other good practices adopted in the information security strategy. As of today, Cryptology can adapt to every business being incorporated in its best practices of security with a very low expenditure using open sources models like PGP.
The development in information security and cryptology together can help fill the gap in new talent sourcing and development of a national network of a labor force, and difficult attackers from gaining access to sensitive data.
Sources:
www.blackhat.com/presentations/bh-usa-07/De_Haas/Presentation/bh-usa-07-de_haas.pdf
Schneier, Bruce – Applied Cryptography – 2nd Edition.
https://wongmichael.files.wordpress.com/2013/04/model-of-conventional-cryptosystem.png?w=300&h=252
http://truecrypt.sourceforge.net/
About the author Luis Nakamoto
Luis Nakamoto is a Computer Science student of Cryptology and a enthusiastic of information security having participated in groups like Comissão Especial de Direito Digital e-Compliance (OAB/SP) and CCBS (Consciência Cibernética Brasil) as a researcher in new technologies related to ethical hacking, forensics and reverse engineering. Also a prolific and compulsive writer participating as a Redactor to Portal Tic from Sebrae Nacional.
[adrotate banner=”9″]
(Security Affairs – Cryptology , cyber security)
[adrotate banner=”13″]