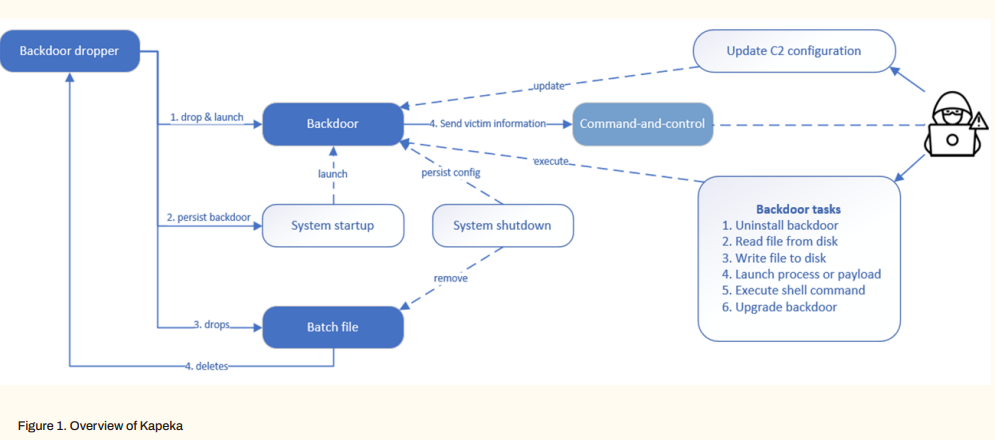
The alleged link between the Shadow Brokers data leak and the Stuxnet cyber weapon

Security researchers who analyzed the documents and hacking tools included in the last Shadow Brokers dump found a link to the Stuxnet virus.
On Friday, the Shadow Brokers leaked a new bunch of files belonging to the alleged NSA arsenal.
Security researchers who analyzed the documents and hacking tools included in the last dump have discovered many exploits specifically designed to compromise Windows systems.
Digging the archive, experts spotted a surprising exploit that was used in the Stuxnet cyber weapon, the malware used to destroy the Iranian nuclear programme in the Natanz plant.
According to Symantec researcher Liam O’Murchu, the exploit was developed for Windows’ MOF files and it is “almost the exact same script” used in Stuxnet.
“There is a strong connection between Stuxnet and the Shadow Brokers dump,” O’Murchu told Motherboard in an email. “But not enough to definitively prove a connection.”
Let’s see the similarities between the Stuxnet code and the exploit code in the last dump leaked by Shadow Brokers.
Below a portion of the script from Stuxnet.
and this is a portion of the script dumped by The Shadow Brokers.

Of course, who has developed the tool included in the Shadow Brokers dump may have borrowed the script from the public knowledge of Stuxnet. The same code, for example, was included in the Metasploit framework allowing anyone to create a MOF file like the one exploited in Stuxnet attack.
O’Murchu highlighted that the MOF file creation tool in the Shadow Brokers dump presented a last compiled date set on September 9, 2010, a few months Stuxnet discovery, but “shortly before the code was added to Metasploit.”
The researcher Kevin Beaumont believe that there is link between Stuxnet and the exploit shared by Shadow Brokers.
https://twitter.com/GossiTheDog/status/852866191920173057
Lorenzo Franceschi-Bicchierai from Motherboard also reported that the Avast Antivirus detects some exploits in the Shadow Brokers dump as Stuxnet.
It is very curious, even in the case of false positive that the signatures of the exploits match the Stuxnet’s one.
Are we facing with the evidence that the NSA-linked Equation Group was involved in the Stuxnet attack, or is this a well organized false-flag operation?
“Therefore, the Stuxnet MOF file creation tool that the Shadow Brokers dropped on Friday is possibly the earliest technical evidence that NSA hackers and developers coded Stuxnet, as many suspect.” added Bicchierai.
[adrotate banner=”9″]
Pierluigi Paganini
(Security Affairs – NSA, Shadow Brokers)