
Security experts at IBM reported a spike in the number of cyber attacks pushing a variant of the popular C99 webshell in February and March, a 45 percent increase compared to the previous period. The C99 variant used in the attacks is currently detected by 37 of 56 antivirus software.
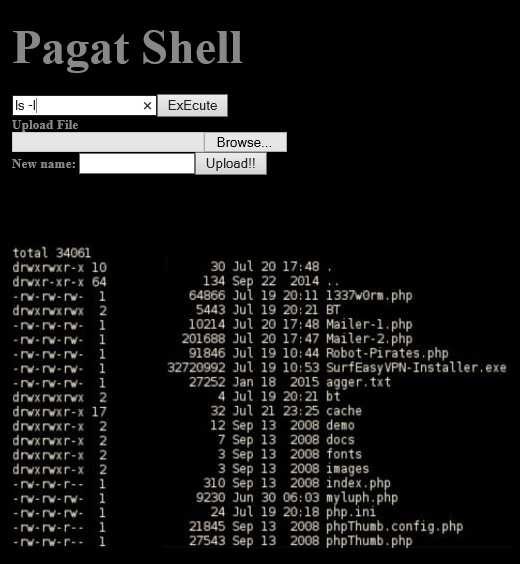
The experts noticed a common URL and file name, pagat.txt, in the attacks. The file includes an obfuscated PHP script, the attackers hide in this way a malicious code used to bypass the Web application firewall (WAF) that may be used to protect the website.
When the script is executed on the target system, an email is sent back to the attacker notifying that the server has been compromised.
Below the GET request observed in the attacks:
hxxp://www.victim.com/wp-content/themes/twentythirteen/pagat.txt.
Googling the pagat.txt file it is possible to have an idea of the number of compromised machines.
The C99 webshell installed on the server could be accessed from a browser and used to launch shell commands on the target. The attacker can use it to perform several actions, including the upload of malicious payloads.
“Most of the time, these webshell entry points result from vulnerabilities in third-party plugins (which we know often don’t undergo any security review during development) or an unpatched bug in the parent application. In fact, according to IBM X-Force, the largest percentage of CMS vulnerabilities are found in plugins or modules written by third parties.” reported IBM.
The researcher discovered that the specific variant of the C99 webshell used in the recent attacks is the same used by the Indonesian hacker Hmei7, that defaced more than 150,000 websites from all across the world.
In order to protect your website ensure that your WordPress installation is not affected by known vulnerabilities, install security plugins, and change default settings.
[adrotate banner=”9″]
(Security Affairs – C99 Webshell, hacking)